CVE-2025-61161 - DLL Hijacking in Evope.Service via Missing wtsapi32.dll – SYSTEM to GUI Shell
Summary
A privilege escalation vulnerability was discovered in Evope.Service, where a missing dependency (wtsapi32.dll) loaded from the application directory allows an attacker to execute arbitrary code with NT AUTHORITY\SYSTEM privileges.
By placing a crafted wtsapi32.dll alongside the vulnerable binary, an attacker can exploit this DLL hijack to launch a cmd.exe shell as SYSTEM inside the GUI session of the logged-in user, breaking the Session 0 isolation model.
This vulnerability was exploited using a custom payload and is currently unpatched.
Discovery Process
The vulnerability was identified during a routine analysis of the Evope.Collector component, which is launched by the Evope.Service.exe process running under SYSTEM.
By using Process Monitor, DLL search order activity was analyzed during service startup.
Step 1: Initial Execution Monitoring
The Evope.Service.exe process was started, which in turn loads Evope.Collector.exe. Process Monitor revealed a series of NAME NOT FOUND results for DLLs attempted to be loaded from non-standard paths.
Step 2: Isolating the Hijack Opportunity
One specific line in the capture showed the issue:
- Process Name:
Evope.Service.exe - Operation:
CreateFile - Path:
C:\ProgramData\Evope\wtsapi32.dll - Result:
NAME NOT FOUND
This indicates that Evope.Service.exe, attempts to load wtsapi32.dll from its working directory, falling back to System32 only afterward a well-known pattern vulnerable to DLL hijacking.
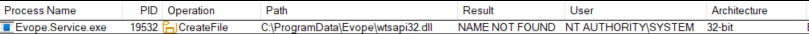
The DLL is missing by default, making it a prime candidate for hijacking when placed in the same directory.
Vulnerability Details
- Type: DLL Hijacking
- Vulnerable Component:
Evope.Service.exe(running as SYSTEM) - Missing DLL:
wtsapi32.dll - Impact: Arbitrary code execution as SYSTEM
- Scope: Code is executed in Session 0, but can be elevated to GUI with crafted payload
- Affected privilege context: SYSTEM
The binary is executed as a service or background task under SYSTEM. By creating a malicious wtsapi32.dll in the same directory, the process loads it with full privileges.
Exploitation
1. Crafting the Malicious DLL
A custom wtsapi32.dll was developed and compiled using MinGW:
└─$ i686-w64-mingw32-gcc wtsapi32.c -shared -ladvapi32 -lwtsapi32 -luserenv -o wtsapi32.dll2. Payload Behavior
The payload DLL uses the DllMain entry point to:
- Obtain the SYSTEM token of the current process.
- Duplicate the token and assign the session ID of the logged-in user.
- Use
CreateProcessAsUser()to launch a visiblecmd.exeas SYSTEM inside the interactive user session (e.g., Session 1).
Demonstration
After dropping the malicious wtsapi32.dll in the Evope.Service installation path C:\ProgramData\Evope\, the next time the binary is launched as SYSTEM, it loads the DLL and executes the payload.
Result:
cmd.exeis spawned in the user's desktop session.- The shell runs as NT AUTHORITY\SYSTEM.
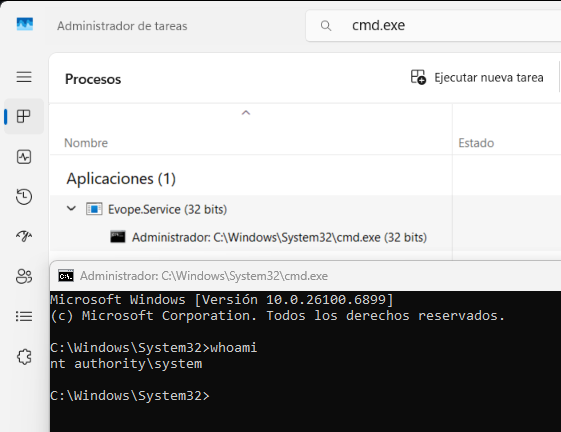
- The SYSTEM
cmd.exewindow visible in the user session.- The output of
whoamishowingnt authority\system.- Task Manager shows CMD as a child process of
Evope.Service.
Mitigation Recommendations
To mitigate this vulnerability, the following actions are recommended:
- Always use fully qualified paths when loading system libraries.
- Avoid relying on DLLs that may not be present in the target environment.
- Ensure the application directory is not writable by low-privileged users.
- Implement secure DLL search path practices:
- Use
SetDefaultDllDirectories()withLOAD_LIBRARY_SEARCH_SYSTEM32. - Call
AddDllDirectory()explicitly if needed.
- Use
- Digitally sign and verify loaded DLLs in sensitive services.
Disclosure Status
- CVE Requested: Yes
- CVE ID: CVE-2025-61161
- Vendor Notified: Yes
- Exploit Published: No (controlled PoC only)
- Affected Version: Evope Collector Collector 1.1.6.9.0, Core 1.1.3.2.4, Update 1.1.0.3.6